In March 2020, Microsoft intends to change the default behaviour of the Microsoft LDAP servers that are part of an Active Directory deployment. These changes will make secure LDAP channel binding and LDAP signing a default requirement when accessing Microsoft Active Directory using LDAP or LDAPS.
Any system that connects to Active Directory via LDAP without using TLS will be negatively affected by this change. Here Microsoft provides ways to find clear-text connections to your Active Directory.
How does this affect vScope & our users?
If configured, vScope interacts with Microsoft Active Directory with two functionalities:
- Directory integration – The Active Directory is integrated with vScope for users to log in with their user accounts. This is configured under Settings.
- During discovery – When inventorying the Active Directory. This is configured in the Discovery Manager.
vScope already has support for secure LDAP channel binding and LDAP signing, but it haven’t been a default setting up until now. If you aren’t using the secure LDAP channel binding and LDAP signing when the changes hit in march, you will be locked out of vScope and/or lose your Active Directory inventory.
How do I configure vScope to use the correct settings?
1. Directory integration
Important: Before making changes to the directory integration we recommend to creating a local vScope administrator under “Users & Groups” in vScope. So you can access vScope if the LDAP connection would fail.
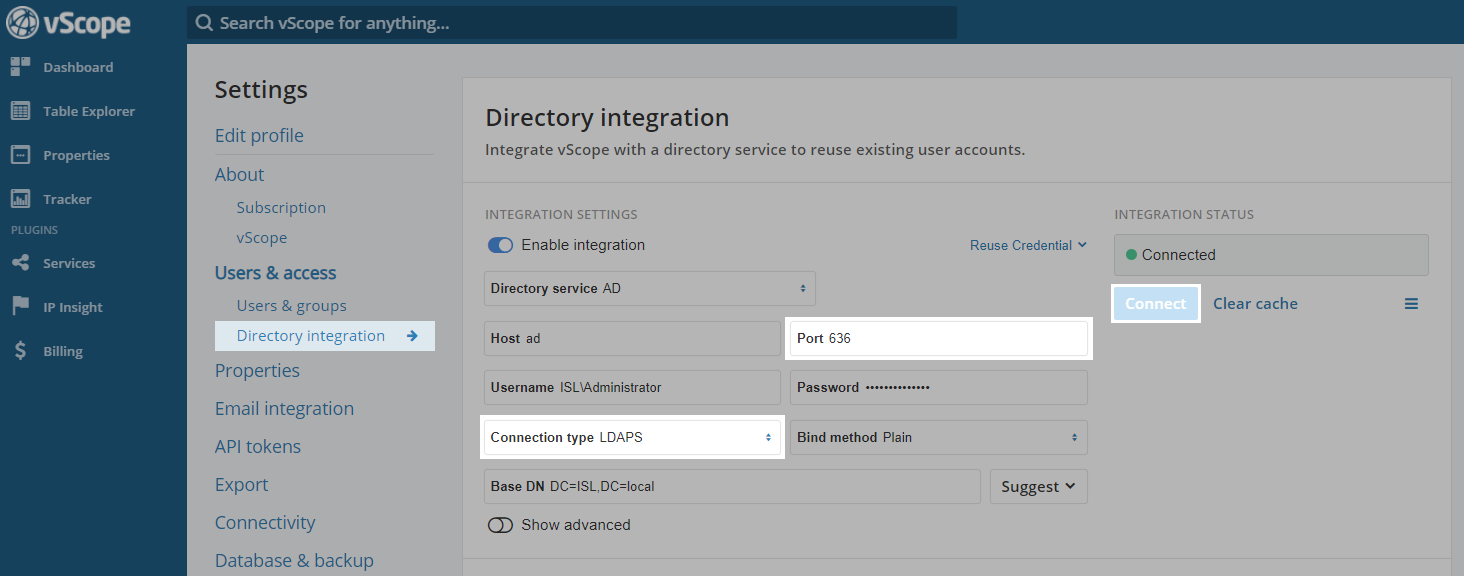
The settings for the directory integration can be found in Settings -> Directory integration -> Integration settings.
- Change the connection to LDAPS and click connect. The bind method can be “Plain”.
- Ensure that the correct port is set up for LDAPS. Default for LDAPS is “636”.
- Click on connect.
2. During discovery
To change to LDAPS for the active directory inventory you need to update the LDAP credential.
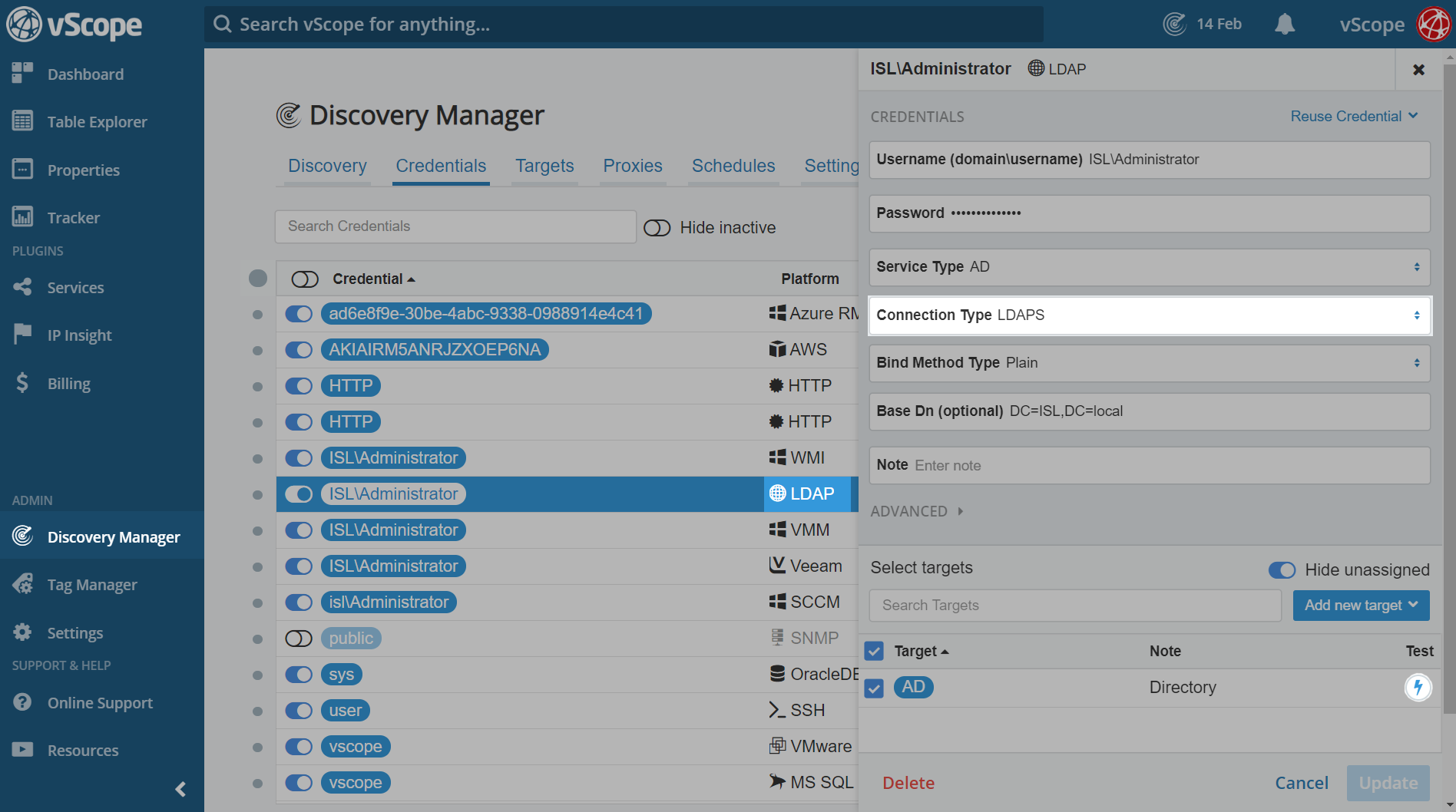
- Go to Discovery Manager -> Credential. Find the LDAP credential in the credential list and click on it.
- Change the connection type to LDAPS and click update in the bottom right corner. Bind method can still be plain.
- You can test the AD connection with the LDAPS settings by clicking on the lightning button.
- Update the credential.